Is your computer malfunctioning due to viruses? Most of the computer users experience the save quite often. To protect your PC from a virus attack, you should understand exactly what a virus is. Computer virus is a software program which is designed with malicious intentions. It is not very difficult to keep your computer running like a brand new-one with the regular maintenance and updation of your anti virus software from time to time. It is basically spread via internet. In this article we have discussed about some of the best ways to protect your computer from viruses and spyware.
Is your computer malfunctioning due to viruses? Most of the computer users experience the save quite often. To protect your PC from a virus attack, you should understand exactly what a virus is. Computer virus is a software program which is designed with malicious intentions. It is not very difficult to keep your computer running like a brand new-one with the regular maintenance and updation of your anti virus software from time to time. It is basically spread via internet. In this article we have discussed about some of the best ways to protect your computer from viruses and spyware. -
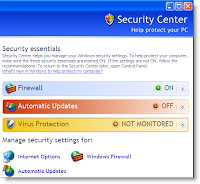
For better computer protection, you should use an Internet firewall. Operating systems like Windows 7, Windows Vista, and Windows XP with SP2 comprise built-in firewall and this is turned on by default. Check whether it is on or not. If not, turn it on.
-
You should also update the operating system regularly as Microsoft releases updates to protect the users from virus attack. Have you installed the most recent version of Microsoft Office? Your Microsoft Office programs will also be updated by Microsoft Update.
-
It is a must to install an antivirus software program and update it regularly. AVG, Avast, Norton, Macafee, etc. are some of the most renowned names in this regard. You can start with the trial version and if you find it satisfactory, then go for the paid version.
-
It is also suggested not to open an e-mail attachment from an unknown source. In most of the cases, these attachments contain viruses and spyware. You should also use strong passwords to protect your computer from unwanted access.
Source:- www.mytechsupportstore.com